Information Security
Is one of the sensitive areas in computer science (even, if there is a lot of information that won't be stored electronically, i.e. all are in scope), due to the effect.
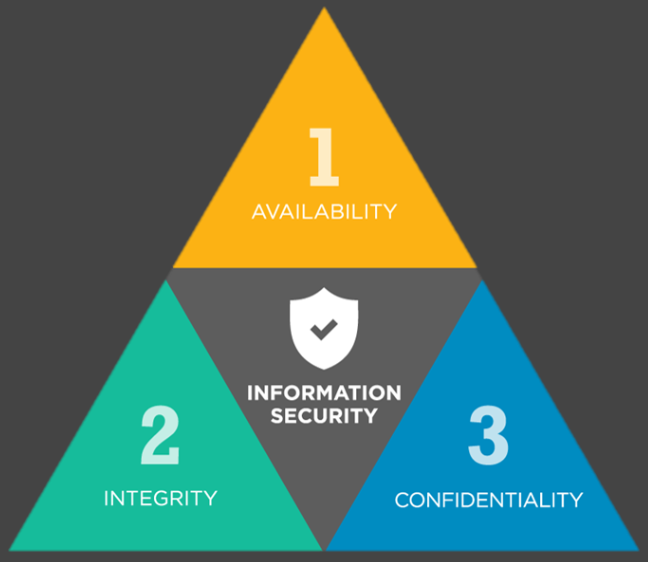
IS defined as: protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction in order to provide the three major basics of information security: confidentiality, integrity, availability “CIA triad” , and in addition other basics such as authenticity, and non-Repudiation can also be involved.
Information security should be considered as a basis and not an option.
Information Security Policy
The information security policy is a set of process management strategies and policies aimed at protecting, detecting, identifying and countering threats targeting digital or non-digital information. Among its responsibilities, the information security policy must establish a set of business processes that will protect information assets regardless of the format or the state of the information (in transit, in process, or stored at rest).
In this regard, our role is:
- To develop or maintain the security policies and procedures.
- Ensuring compliance with those policies and procedures are consistently applied in all solutions, projects, and initiatives.
- Ensuring the Risk Management through Risk Analysis to identify and avoid predicted risks.
Let's look at more factors in information security:
Security Governance
Security governance is the combined set of tools, personnel, and processes that provide for formalized risk management.

Compliance
Security compliance is the act of steps and procedures an enterprise takes to ensure that business comply with the respective regulations. Therefore, Compliance ensure companies do the best practices to protect their systems, data, and operations.

Process
Security process/procedure

Security procedures are steps and tasks necessary to ensure security in the daily operations of an organization. Security procedures work in conjunction with security policies, standards, and guidelines to implement the outlines of safety operations within any business.
